Nearly half of organizations are not using the full set of features and applications available in Microsoft 365, a research from Ensono reveals. Most notably, many enterprises are neglecting the cybersecurity features available in the platform, leaving them open to vulnerabilities.
Since the onset of the pandemic, platforms and tools such as Microsoft 365 have enabled businesses to successfully adapt to the new working world.
Ensono surveyed IT decision makers who use Microsoft 365 to understand how organizations configure the platform for their businesses. 83% of those surveyed stated that their current Microsoft 365 arrangement is invaluable to effective business operations, while 72% believe the current setup provides value for money.
Although most businesses are happy with their Microsoft 365 set up, many are not taking full advantage of what the package has to offer. In particular, a large proportion of companies are not making use of built in security features.
Key findings
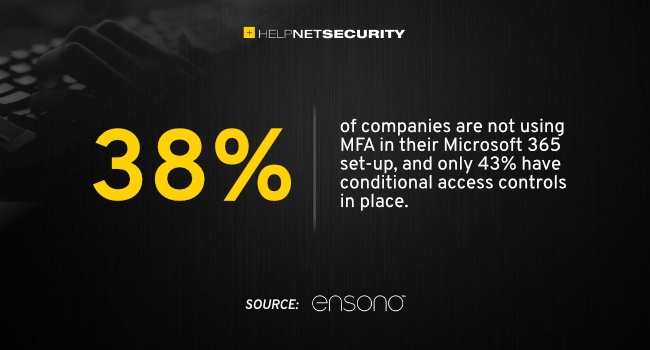
- 38% are not using multi-factor authentication (MFA)
- Only 43% have Conditional Access Controls in place (CAC)
- 46% do not have data loss prevention (DLP) or data classification configuredOf those surveyed that reported a Microsoft 365-related breach, 42% were linked to files being shared with external parties and 37% were due to the impersonation of a compromised account. These incidents could be better protected against with the correct implementation of MFA and CAC.
Simon Ratcliffe, Principal Consultant at Ensono, said: “While Microsoft 365 has proven invaluable for enterprises undergoing rapid transformation, not all companies have set up the platform in an optimal manner for their business. Microsoft 365 licensing inefficiencies remain a persistent problem in the market today, with firms creating additional costs by investing in third party tools already available as part of their Microsoft 365 package. With optimisation and the implementation of key security features, the platform can provide a better and more secure experience for its users.
“However, there is no one-size-fits-all solution for every business. Each organization is unique, and therefore security requirements and the needs of users will vary. When reviewing an organization’s Microsoft 365 configuration, it is essential that the process is led every step of the way by the business context. Following a review, the Microsoft 365 environment can be optimised for specific business requirements, including maximising the use of Microsoft 365 features to match the needs of the organization, and creating a security set-up tailored to the cybersecurity posture of the business.”
Click here to view original web page at www.helpnetsecurity.com