SMBs can obtain advice about cybersecurity quite easily from a plethora of resources. Getting their hands on practical technology solutions is, on the other hand, more of a problem, as they are often greatly constrained by their budget. Still, there are solutions within their reach.
Extreme risks shouldn’t be left unaddressed, because cyberattacks against SMBs are too common and attackers still successfully exploit human weaknesses, primarily via email.
Confirm your pain points
Attacks via email can escalate into malware infections and other incidents that lead to financial loss, identity threat, and loss of access to IT assets. Security fundamentals will fall into the following buckets (and email security cuts across several):
- Email security
- Backup
- Least privilege computing
- Network security
- Identity management and access control
- Security awareness training
- Administrative controls
- Physical controls
Risk management: Your initial (and free) blueprint for getting started
Trouble is brewing if any of those categories have inadequate controls. A successful attack via email can rapidly lead to compromised access control, exfiltration of protected information, and can adversely impact network stability and mission critical system operations. We know this because it happens every day, despite current SMB cybersecurity strategies.
Risks persist in every inbox. The question is what an SMB can realistically do to adequately identify their risk level and plan for when an incident occurs.
There are a variety of templates and formulas for calculating risks, and they can serve as a guide for assessing whether an SMB’s existing controls are adequate to safeguard the confidentiality, integrity, and availability of its assets.
Take a moment to map your risks according to the chart below.
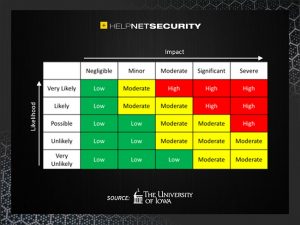
It’s unlikely that an SMB will get a “green” on all aspects. It’s not for lack of trying or knowledge – it’s just unrealistic for a small organization to be constantly on top of everything or to have that capacity.
It shouldn’t take very long to determine that network security is an extreme risk if it’s not well controlled. You may have an EDR system or basic spam filtering, but threat actors are inventive and are continually developing new methods of attack.
It’s unrealistic to expect SMBs will keep pace to reliably prevent every new line of attack, but it makes sense for IT teams to consider new approaches that provide an affordable defense-in-depth strategy.
Practical and affordable cybersecurity solutions to mitigate risks
Most of what you should be doing involves people and their awareness of security issues, the systems that they use, and how much of a risk inexistent or inadequate controls present.
If you have identified the risks but don’t know where to start, know that there are services customized for SMBs and financially structured to meet tight budgets. One practical and immediate starting point is the Small Business Administration, a centralized information hub that will practically guide you through the whole process.
Click here to view original web page at www.helpnetsecurity.com








